Anomaly Based Ids Examples

A Anomaly Based Intrusion Detection System B Signature Based Download Scientific Diagram


An Anomaly Based Intrusion Detection System Ids Using Datamining To Download Scientific Diagram

Anomaly Based Intrusion Detection Systems The Requirements Methods Measurements And Datasets Hajj 2021 Transactions On Emerging Telecommunications Technologies Wiley Online Library

Signature And Anomaly Based Ids 5 Download Scientific Diagram
Signature Based Vs Anomaly Based Methods Of Intrusion Detection Download Scientific Diagram
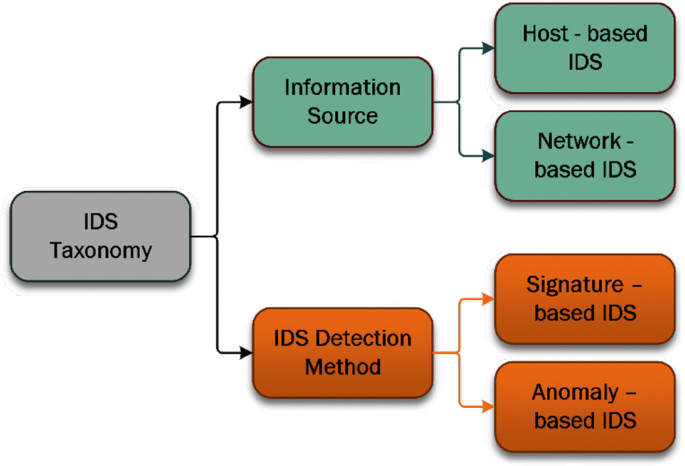
Anomaly Based Intrusion Detection System Using Multi Objective Grey Wolf Optimisation Algorithm Springerlink
Anomaly Based Methodology Architecture Download Scientific Diagram
Comments
Post a Comment